Friends and Colleagues,
It is critical that at this time, the Digital Edge Security Team sends an urgent warning about a wide-spread email phishing campaign aiming at Microsoft Office 365 users. The emails have subject similar to this: “View your Office 365 Business billing statement for…”.
The email looks very real and our Security Team is urging what users should pay attention to when analyzing such email for authenticity.
Multiple clients have notified us about receiving said emails and some people were getting trapped by this campaign.
The email would look like this:
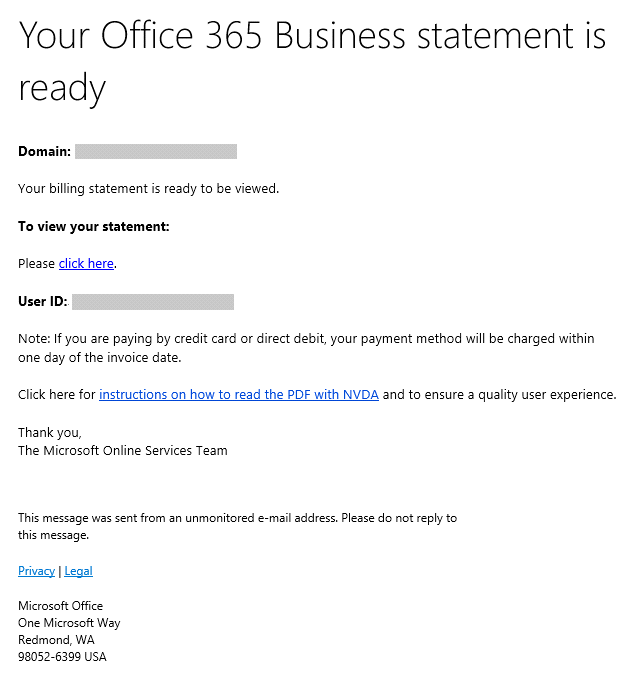
The email looks like it came from Microsoft, however when you hover over the link, it would show that the actual redirect is not Microsoft but something like this:
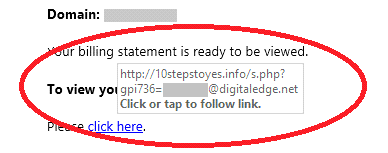
Here is what Digital Edge knows:
1. Emails are coming from random email addresses, mostly IT companies.
2. Actual origination of emails is different and most likely are from infected home or small business computers. Here is an example of the envelope:
Received: from 50-194-90-241-static.hfc.comcastbusiness.net ([50.194.90.241] helo=inreachitsolutions.com)
by digitaledge.net xxxxxx with smtp
(Exim MailCleaner)
id 1e9F8d-0000yk-D7
for <xxxxxxx@digitaledge.net>
from <microsoft@inreachitsolutions.com>; Mon, 30 Oct 2017 14:50:19 -0400
X-MailCleaner-SPF: none
Message-ID: <A231B219.9F021ACC@inreachitsolutions.com>
Date: Mon, 30 Oct 2017 14:51:31 -0400
Reply-To: Microsoft Online Services Team <microsoft@inreachitsolutions.com>
From: Microsoft Online Services Team <microsoft@inreachitsolutions.com>
X-Mailer: Apple Mail (2.1510)
3. Users trapped by the email report that the redirect takes them to Microsoft like page that asks to login to your Office 365 account.
4. After user logs in, the perpetrator collects login credentials and sets up hidden rules in Office 365 email.
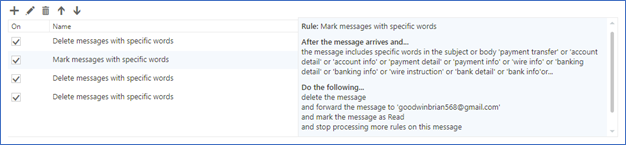
5. After sometime users in the organization starts receiving fraudulent email asking to transfer money.
Good thing:
- Those attacks are not targeted and are using opportunistic methods to spy on company’s emails and then try to trick executive and financial departments to transfer money.
Bad things:
- Those emails look very authentic. It is easy to fall in the trap if you use Office 365.
- The speed of setting up rules are showing that there is a good level of automation in setting up rules in Office 365.
Steps Digital Edge team is taking to help our clients:
1. Update anti-spam rules to block such emails. (Notice no SPF record).
2. We develop alerts on logs from Office 365 and alert on rule setup events. More details:
Digital Edge operates large log management infrastructure based on Elasticsearch Logstash Kebana (ELK). Our team is working on setting up alert logic to notify admins about rules being setup in Office 365.
Please contact the Digital Edge security team for more information or immediate help for configuring your Office 365 Rules and Alerts.
